HP Inc. (NYSE: HPQ) today released a new report highlighting the far-reaching cybersecurity implications of failing to secure devices at every stage of their lifecycle. The findings show that platform security – securing the hardware and firmware of PCs, laptops and printers – is often overlooked, weakening cybersecurity posture for years to come.
The report, based on a global study of 800+ IT and security decision-makers (ITSDMs) and 6000+ work-from-anywhere (WFA) employees, shows that platform security is a growing concern with 81% of ITSDMs agreeing that hardware and firmware security must become a priority to ensure attackers cannot exploit vulnerable devices. However, 68% report that investment in hardware and firmware security is often overlooked in the total cost of ownership (TCO) for devices. This is leading to costly security headaches, management overheads and inefficiencies further down the line.
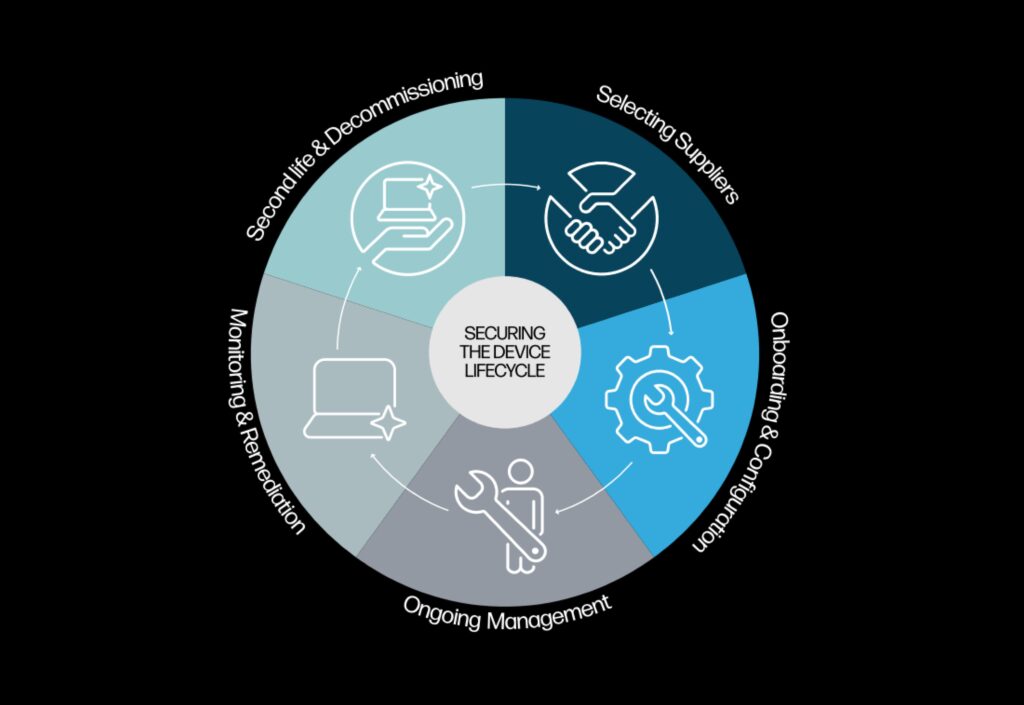
Key findings from across the five stages of the device lifecycle include:
1. Supplier Selection – In addition, 34% say a PC, laptop or printer supplier has failed a cybersecurity audit in the last five years, with 18% saying the failure was so serious that they terminated their contract. 60% of ITSDMs say the lack of IT and security involvement in device procurement puts the organization at risk.
2. Onboarding and Configuration – More than half (53%) of ITSDMs say BIOS passwords are shared, used too broadly, or are not strong enough. Moreover, 53% admit they rarely change BIOS passwords over the lifetime of a device.
3. Ongoing Management – Over 60% of ITSDMs do not make firmware updates as soon as they’re available for laptops or printers. A further 57% of ITSDMs say they get FOMU (Fear Of Making Updates) in relation to firmware. Yet 80% believe the rise of AI means attackers will develop exploits faster, making it vital to update quickly.
4. Monitoring and Remediation – Every year, lost and stolen devices cost organizations an estimated $8.6bn . One in five WFA employees have lost a PC or had one stolen, taking an average 25 hours before notifying IT.
5. Second Life and Decommissioning – Nearly half (47%) of ITSDMs say data security concerns are a major obstacle when it comes to reusing, reselling, or recycling PCs or laptops, while 39% say it’s a major obstacle for printers.
“Buying PCs, laptops or printers is a security decision with long-term impact on an organization’s infrastructure. The prioritization, or lack thereof, of hardware and firmware security requirements during procurement can have ramifications across the entire lifetime of a fleet of devices – from increased risk exposure, to driving up costs or negative user experience – if security and manageability requirements are set too low compared to the available state of the art,” warns Boris Balacheff, Chief Technologist for Security Research and Innovation at HP Inc.
Balacheff continues: “It’s essential that end-user device infrastructures become resilient to cyber risks. This starts with prioritizing the security of hardware and firmware and improving the maturity of how they are managed across the entire lifecycle of devices across the fleet.”
From factory to fingertips – oversights in the supplier selection process, and onboarding and configuration limitations, impact device security across the lifecycle
The findings highlight the growing need for IT and security to be part of the procurement process for new devices, to set the requirements and verify vendor security claims:
• 52% of ITSDMs say procurement teams rarely collaborate with IT and security to verify suppliers’ hardware and firmware security claims.
• 45% of ITSDMs admit they have to trust suppliers are telling the truth as they don’t have the means to validate hardware and firmware security claims in RFPs.
• 48% of ITDMS even say that procurement teams are like “lambs to the slaughter” as they’ll believe anything vendors say.
IT professionals are also concerned about the limitations of their ability to onboard and configure devices down to the hardware and firmware level seamlessly.
• 78% of ITSDMs want zero-touch onboarding via the cloud to include hardware and firmware security configuration to improve security.
• 57% of ITSDMs feel frustrated at not being able to onboard and configure devices via the cloud.
• Almost half (48%) of WFA workers who had a device delivered to their home complained that the onboarding and configuration process was disruptive.
“You will always need to choose technology providers you can trust. But when it comes to the security of devices that serve as entry points into your IT infrastructure, this should not be blind trust,” comments Michael Heywood, Business Information Security Officer, Supply Chain Cybersecurity at HP Inc. “Organizations need hard evidence – technical briefings, detailed documentation, regular audits and a rigorous validation process to ensure security demands are being met, and devices can be securely and efficiently onboarded.”
Challenges and frustrations around the ongoing management, monitoring and remediation of devices
71% of ITSDMs say the rise in work-from-anywhere models has made managing platform security more difficult, impacting worker productivity and creating risky behaviors:
• One in four employees would rather put up with a poor-performing laptop than ask IT to fix or replace it because they can’t afford the downtime.
· 49% of employees have sent their laptop to be repaired, and say this took over 2.5 days to fix or replace the device, forcing many to use their personal laptop for work, or to borrow one from family or friends – blurring the lines between personal and professional use.
• 12% had an unauthorized third-party provider repair a work device, potentially compromising platform security and clouding IT’s view of device integrity.
Monitoring and remediating hardware and firmware threats to prevent threat actors accessing sensitive data and critical systems is vital. However, 79% of ITSDMs say their understanding of hardware and firmware security lags behind their knowledge of software security. Moreover, they lack mature tools that would give them the visibility and control they would want to manage hardware and firmware security across their fleets:
• 63% of ITSDMs say they face multiple blind spots around device hardware and firmware vulnerabilities and misconfigurations.
• 57% cannot analyze the impact of past security events on hardware and firmware to assess devices at risk.
• 60% say that detection and mitigation of hardware or firmware attacks is impossible, viewing post-breach remediation as the only path.
“Post-breach remediation is a losing strategy when it comes to hardware and firmware attacks,” warns Alex Holland, Principal Threat Researcher in the HP Security Lab. “These attacks can grant adversaries full control over devices, embedding deep within systems. Traditional security tools are blind to these threats as they tend to focus on the OS and software layers, making detection nearly impossible. Preventing or containing these attacks in the first place is critical to stay ahead, or else organizations risk a threat they cannot see – and cannot remove.”
Second life and decommissioning – how data security concerns are leading to an e-waste epidemic
Platform security concerns are also impeding organizations’ ability to reuse, recycle or resell end of life devices:
• 59% of ITSDMs say it’s too hard to give devices a second life and so they often destroy devices over data security concerns.
• 69% say they are sitting on a significant number of devices that could be repurposed or donated if they could sanitize them.
• 60% of ITSDMs admit their failure to recycle and reuse perfectly usable laptops is leading to an e-waste epidemic.
Complicating matters further, many employees sit on old work devices. This not only prevents devices from being repurposed, but it also creates data security risks around orphaned devices that still may carry corporate data.
• 70% of WFA employees have at least 1 old work PC/laptop at home or in their office workspace.
• 12% of WFA workers have left a job without returning their device right away – and almost half of these say they never did.
“IT teams are hoarding end-of-life devices because they lack the assurance that all sensitive company or personal data has been fully wiped – which in itself can pose data security risks and negatively impact ESG goals. Finding a reputable IT asset disposition vendor that uses the latest industry-standard erasure or media-destruction processes and provides a data sanitization certificate so you can meet compliance requirements, is key,” comments Grant Hoffman, SVP Operations and Portfolio, HP Solutions.
A new approach to the device lifecycle is needed to improve platform security
More than two thirds (69%) of organizations say their approach to managing device hardware and firmware security only addresses a small part of their lifecycle. This leaves devices exposed, and teams unable to monitor and control platform security from supplier selection to decommissioning.
To manage platform security across the entire lifecycle, HP Wolf Security’s recommendations include:
• Supplier selection: Ensure IT, security and procurement teams work together to establish security and resilience requirements for new devices, validate vendor security claims and audit supplier manufacturing security governance.
• Onboarding and configuration: Investigate solutions that enable secure zero-touch onboarding of devices and users, and secure management of firmware settings that don’t rely on weak authentication like BIOS passwords.
• Ongoing management: Identify the tools that will help IT monitor and update device configuration remotely and deploy firmware updates quickly to reduce your fleet’s attack surface.
• Monitoring and Remediation: Ensure IT and security teams can find, lock and erase data from devices remotely – even those that are powered down – to reduce the risk of lost and stolen devices. Improve resilience by monitoring device audit logs to identify platform security risks, such as detecting unauthorized hardware and firmware changes and signs of exploitation.
• Second life and decommissioning: Prioritize devices that can securely erase sensitive hardware and firmware data to enable safe decommissioning. Before redeploying devices, seek to audit their lifetime service history to verify chain of custody, and hardware and firmware integrity.
For further insights and recommendations download the full report ‘Securing the Device Lifecycle: From Factory to Fingertips, and Future Redeployment’ here: link
1. WFA sample: A survey of 6,055 office workers that work hybrid, remotely or from anywhere in the US, Canada, UK, Japan, Germany and France. Fieldwork was undertaken from 22nd – 30th May 2024. The survey was carried out online by Censuswide.
2. ITSDM sample: A survey of 803 IT and security decision makers in the US, Canada, UK, Japan, Germany and France. Fieldwork was undertaken from 22nd February – 5th March 2024. The survey was carried out online by Censuswide.
HP Inc. (NYSE: HPQ) is a global technology leader and creator of solutions that enable people to bring their ideas to life and connect to the things that matter most. Operating in more than 170 countries, HP delivers a wide range of innovative and sustainable devices, services and subscriptions for personal computing, printing, 3D printing, hybrid work, gaming, and more. For more information, please visit: http://www.hp.com.
About HP Wolf Security
HP Wolf Security is world class endpoint security. HP’s portfolio of hardware-enforced security and endpoint-focused security services are designed to help organizations safeguard PCs, printers, and people from circling cyber predators. HP Wolf Security provides comprehensive endpoint protection and resiliency that starts at the hardware level and extends across software and services. Visit https://hp.com/wolf.

